- Qualcomm Launches Snapdragon 4 Gen 2 Mobile Platform
- AMD Launches Ryzen PRO 7000 Series Mobile & Desktop Platform
- Intel Launches Sleek Single-Slot Arc Pro A60 Workstation Graphics Card
- NVIDIA Announces Latest Ada Lovelace Additions: GeForce RTX 4060 Ti & RTX 4060
- Maxon Redshift With AMD Radeon GPU Rendering Support Now Available
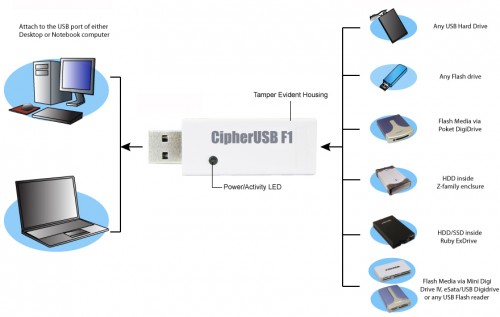
Addonics CipherUSB Review – Portable Encryption Made Easy

As important as data encryption can be for the home user, it’s even more imperative in the enterprise. The problem? The most effective measures are usually cast aside in lieu of something a little easier to deal with. With the CipherUSB, Addonics hopes to bring “simple” and “most effective” together as one. Does it succeed?
Page 3 – Highlights & Final Thoughts
Though my above points are certainly things that I hope Addonics takes to heart, I have to give the company some serious points for adding a product to its lineup that does exactly what it’s supposed to do – make storage encryption simple. If the password strings themselves are complex enough and protected appropriately, the devices can be programmed once and handed out to staff as needed.
Throughout all of this review, I haven’t really touched much on the subject of price, and that’s because it’s frankly negligible for what the CipherUSB actually offers. ECB FLE models cost $39.95, and CBC is $69.95. Add $10 to either if you want Mac compatibility as well. For the convenience and the fact that you don’t need one device per person or per storage device, this is practically a steal.
Is there room for improvements? Yes, and some of them really need to be made (like the file extension issue). The software should be redesigned for its target market, but it does work. Overall, the device lacks polish, not function. However, the couple glaring flaws it has are very large indeed, impacting both usability and security – which are the two things it’s supposed to have.
All of this puts me in an unfortunate position as a reviewer – If Addonics puts just a little more work in (even if only to handle the file extension issue), the CipherUSB CBC FLE would be a no-brainer recommendation. As it stands right now, though, it’s some great hardware with promise if only someone would clean up the UI… and that’s a little harder to swallow, since the hardware isn’t designed by Addonics. In fact, the only real place Addonics can actually add to the value chain here and leave its own mark (aside from just being the best company to market Enova’s device in a different country) is the software, so skipping this is just a bitter pill overall.

We’ve contacted Addonics to see what’s coming up, and the company has stated that it does intend to improve the application. For the time being, though, I can’t really give a firm “recommended” or “avoid this.” If what you want is simple but strong encryption without any bells or whistles and you’re willing to develop a strong enough passphrase that it can’t get bruteforced, you needn’t look farther than the CipherUSB. However, a little extra work by Addonics would go a long way to turning this from “does what it says on the label” to “you really should be using one of these.”
tl;dr: If you’re not using Linux, not picky about the interface and you don’t mind the unchangeable “.Addonics” giveaway file extension, the simple-to-use security of the CipherUSB is incredibly versatile and well worth the low price. However, there’s a lot of room for improvement in the software itself, and the file extension can be a security risk that reduces powerful AES256 encryption to a basic dictionary attack.
Support our efforts! With ad revenue at an all-time low for written websites, we're relying more than ever on reader support to help us continue putting so much effort into this type of content. You can support us by becoming a Patron, or by using our Amazon shopping affiliate links listed through our articles. Thanks for your support!