- Qualcomm Launches Snapdragon 4 Gen 2 Mobile Platform
- AMD Launches Ryzen PRO 7000 Series Mobile & Desktop Platform
- Intel Launches Sleek Single-Slot Arc Pro A60 Workstation Graphics Card
- NVIDIA Announces Latest Ada Lovelace Additions: GeForce RTX 4060 Ti & RTX 4060
- Maxon Redshift With AMD Radeon GPU Rendering Support Now Available
TrueCrypt Primer: Part 1 – What It Is & Why You Should Care

We’ve talked a lot in the past about keeping your computer safe and data backed-up, but we haven’t delved much into keeping your data secure. In this first part to a three-part series, we’re taking a look at one of the best (and easiest-to-use) cross-platform solutions for keeping your important data encrypted: TrueCrypt.
Page 3 – Encryption and Performance
TrueCrypt uses On-The-Fly encryption. What this means is that data isn’t encrypted or decrypted until it is used. A mounted TrueCrypt volume hasn’t been entirely decrypted; only those parts needed for the operating system to recognize it as a new drive is. Individual files inside the volume will only be encrypted or decrypted when being used. This allows for very large TrueCrypt volumes to be quickly mounted and dismounted.
One question that will inevitably arise is how fast TrueCrypt really is. Encrypting and decrypting data is expected to have an impact on disk reading and writing operations, more so when we consider entire operating systems or partitions.
TrueCrypt makes use of two programming methodologies and one technology in order to boost the speed at which encrypted data is read and written to disk. These are Parallelization, Pipelining and Hardware Accelerated Encryption, respectively.
Through Parallelization, TrueCrypt will make use of all available cores on a processor, or all available processors on your computer. Through Pipelining, TrueCrypt allows applications to load (or files to be loaded into applications) without them having to wait to be fully decrypted. Through Hardware Accelerated Encryption (AES), TrueCrypt makes use of hardware-based encryption on processors that support it. A processor supporting the AES instruction set can boost TrueCrypt performance to as much as 8x, according to the TrueCrypt authors.
TrueCrypt doesn’t support the Linux Pipeline subsystem, so TrueCrypt pipelining is only available in Windows. The contribution of pipelining to the overall performance of TrueCrypt can be considered negligible if all you do with TrueCrypt is create File Hosted Volumes and do not perform intensive serial IO actions on the encrypted files; like selecting 50 large pictures for opening in Photoshop.
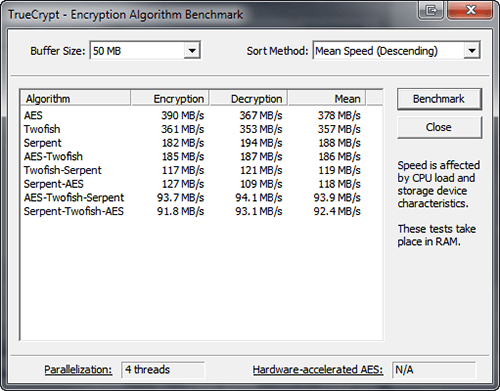
The TrueCrypt benchmark tool
Doing a benchmark analysis of TrueCrypt is beyond the scope of these articles. One reason is because it has been done already. You can find two such articles here and here. TrueCrypt is very fast, even on processors not supporting AES. Parallelization and Pipelining alone can boost the performance to acceptable levels if you are making use of File Hosted Volumes or Partition Hosted Volumes which don’t carry performance-demanding applications. Processors supporting AES will boost performance even further, making the use of a fully encrypted drive very similar to an unencrypted one.
There’s however one thing to keep in mind. Intensive use of disk read/write operations will always augment and underline any IO performance bottlenecks. TrueCrypt isn’t immune. It can never be as fast as a non encrypted disk. Applications that are performance-critical will quickly reveal TrueCrypt associated bottlenecks. You shouldn’t encrypt databases or other IO intensive applications and files if performance is a critical factor.
Support our efforts! With ad revenue at an all-time low for written websites, we're relying more than ever on reader support to help us continue putting so much effort into this type of content. You can support us by becoming a Patron, or by using our Amazon shopping affiliate links listed through our articles. Thanks for your support!




