- Qualcomm Launches Snapdragon 4 Gen 2 Mobile Platform
- AMD Launches Ryzen PRO 7000 Series Mobile & Desktop Platform
- Intel Launches Sleek Single-Slot Arc Pro A60 Workstation Graphics Card
- NVIDIA Announces Latest Ada Lovelace Additions: GeForce RTX 4060 Ti & RTX 4060
- Maxon Redshift With AMD Radeon GPU Rendering Support Now Available
Hello, This Is Yahoo Mail Security, This Is Not A Scam…

On a cold Tuesday morning, a miasma of self-doubt and confusion descended; panic set in from a mysterious phone call. Yahoo found a problem with my account, and I needed to do something about it, fast! ‘This is not a scam’, I was told repeatedly, and that someone had been using my account to do terrible deeds. Except it was a scam, one I’ve heard a hundred times before.
Someone claiming to be from Yahoo’s security department had detected ‘suspicious behavior’ from my ‘system’, and that I need to act quickly to stop further issues arising.
Multiple times I was told, this is not a scam, but the more questions I asked, the more vague the answers became, and none of the details were correct.
When you get a call from anyone with a thick accent, reportedly from the security department of a popular tech company, saying there is suspicious behavior from your ‘device’, you can probably ignore it. Hang up and walk away. The persistence of this attack though, was what made it frustrating.
At around 10am, Tuesday 24th Jan 2017, I received a call from Yahoo Security, to say there was suspicious behavior, and asking if I’ve been noticing any kind of malware on my system. The supposed rep then went on to mention the recent hack and that I may have had my details leaked. Funny how news of a leak can cause people to call you… when the hack actually took place over two years ago, and all passwords have been changed – multiple times – but I’ll humor him.
What is alarming though, is some of the details. They had my full name, where I live, and the exact email address… well, it’s a good thing that email is now only used for potential scams, so it made clarification of this situation quite simple.

It’s A Trap!
The Yahoo security officer, for which I failed to catch his name (not that it would have mattered), went above and beyond to prove his seriousness and authenticity – I mean, you’re never going to check, are you? With each piece of information he gave me, I got bad results. The address? 123 Alex Tower, Birmingham – Fake. I can call them on 08885210120 to confirm it’s Yahoo – Fake. The caller ID on my phone, 002036707630 – not valid, spoofed, fake. This security guy was so secure, that he didn’t exist.
However, I listened and expressed my concerns about this being a scam and then suddenly found the phone-line dead – He’d hung up! Glad that was over, I can now continue eating cold pizza and coffee for breakfast. But then he called back…
He started off as if nothing had happened, and kept sincere, “This isn’t a scam, Jamie, your ‘system’ is showing up as suspicious.” But when pressing them for details about the specifics, the answers turned to questions. This wasn’t just a scam, it was phishing for details. He kept saying ‘system’ or ‘mobile device’ – I know what he’s talking about, but he doesn’t, so he wants me to mention Windows, or Mac, or Android, or iOS, or whatever, then use that to push the conversation forward.
It’s amazing how these individuals can be oddly specific for some things, then completely vague the next. If this was a real threat, they’d have those details already. It would be on their system; the device, the OS, the browser, the IP address, all these wonderful details, so that I can pinpoint the specific device in question and check it. I asked for the IP, it wasn’t mine – despite being logged in. That must mean the hackers are logged in!
We Know Who You Are, But Nothing About You
They kept pressing for what system I was using (like they wouldn’t know). When I let slip I was using a PC, they mentioned that the system was a Windows-based system (shock), and that the serial number had been logged. I asked them for the serial number, to which they happily replied 12 numerical digits… except, Windows serial numbers are not just numbers, but alphanumeric, and typically 25 characters long – but hey, it sounded authentic, right? Plus, this is a hand-made system, it doesn’t have a serial number.
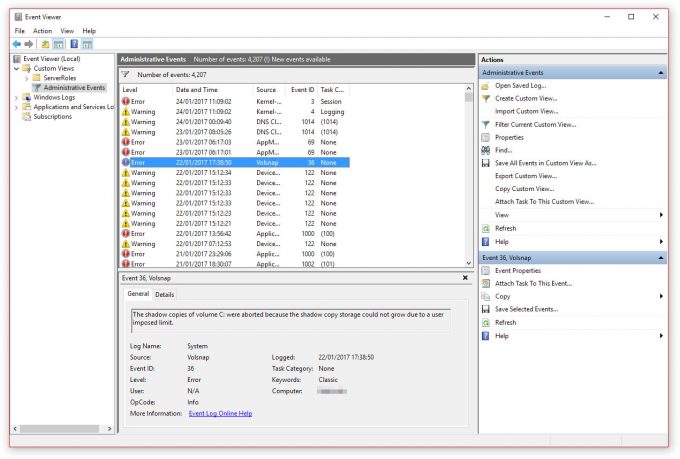
Since I didn’t believe anything he was saying, I hung up abruptly… and then 30 seconds later, they called back again. This must be serious, to call back like that. Desperate to convince me of this issue, he wanted to prove this is real, I then asked, “Is this the part of the scam where you get me to look through event viewer and use the command line?” He affirmed yet again, this is not a scam, and told me to go to Computer Management, look in Event Viewer, Custom Views, Administration Events and holy kettle-bells Batman, look at all those system events; DNS service interruptions, application permission rejections, shadowcopy aborted – I’m being hacked!
Except, I’m not. And isn’t this exactly what I asked him about being the next part of the scam? Event Viewer lists background service logs that Windows hides away and will re-attempt later. They are generic and usually harmless background tasks. And speaking honestly, if there really was malware, do you think it would leave a trace in the event log of the system, saying that it’s being all evil and stealing your bank details? Well, if you continue to follow this ‘security’ rep’s instructions, you will be hacked… or at least, convinced you are.
To The Command Line
If at this point, you were expecting a detailed account of what I did hereafter, you will be sorely disappointed, and for that I apologize. Normally, they then ask you to perform an ipconfig to get IP addresses for your gateway/router, ask you to ping a certain address, and then convince you that these random strings of numbers and active connections are hackers. It was at this point, I said if they call again, I will call the police – they haven’t called again since. But just to be sure, I contacted the police anyway, not that a bunch of spoofed phone numbers will help them much.
When someone over the phone you don’t know, from a seemingly legit company, tells you to do anything with a computer, tell them in no uncertain terms, to go away. In my case, I swore at them repeatedly, which made me feel slightly better, but otherwise a pointless endeavor.
If all this sounds familiar, you’d be right. “Microsoft Security has detected a problem with your computer, you need to act now! Just go to the command line and enter these details, see, look at all these issues! We can make them all go away with our Windows Defender pack, just $250“… except, Windows Defender is free, and pre-installed on every Windows system since Vista.
An attack on the owner of a Yahoo account isn’t anything special, the problem is with the details. They had my name, address, etc, they knew who I was and my home phone number – those were details likely obtained from the hack that happened two years ago that Yahoo only recently disclosed.
The thing is, these details tie in at approximately the same time as another scam was taking place. A call about a questionnaire. BT (British Telecom) were conducting a survey about improving access to Internet services for the elderly, whether the working class should pay more tax, and how the government should improve education about computer related scams (ironic). By answering these questions, they’d send me a cheque for £50! Too good to be true, for sure. The thing is, they had all my details, name, address, phone number – even though I haven’t been signed up with BT in 10 years.
After all the questions answered, all they needed was some kind of contact details to confirm, like a phone number (which they already had) and an email. Let me be clear here, and say that I never give out my main email over the phone. If someone needs it, I give it to them, so under these circumstances, I gave them a disposable account, one of my aged Yahoo accounts. Four days later, I get a call from Yahoo security alerting me to a problem, where they had all my details.
This Ain’t My First Rodeo
I am no stranger to these scams, I get called about them more frequently than I would like, but I keep the conversation succinct with as many profanities as I can muster before they hang up. This particular Yahoo call scam was likely the result of the questionnaire, and they played on the Yahoo leak for authenticity, but how they got my other details remains the question. Was it the hack, or one of the hundreds or thousands of times my details have escaped some company that ‘takes security seriously’? Or was it the thousands of times my details have been sold legally with an opt-out clause requiring written permission to enable – after I’ve given them my details.
The fact remains though, call centers are gearing up and now taking advantage of the Yahoo security breach to flog off their supposed fixes, be it an application or online service that is meant to monitor your details online.
If you get a call regarding security at home, and they persist, threaten to call the police (then actually do so), and this will usually stop them from calling. Also, never do anything they actually say, try to confirm as few details as possible, and never give them new information to play with – remember, they called you, so they already know who you are.
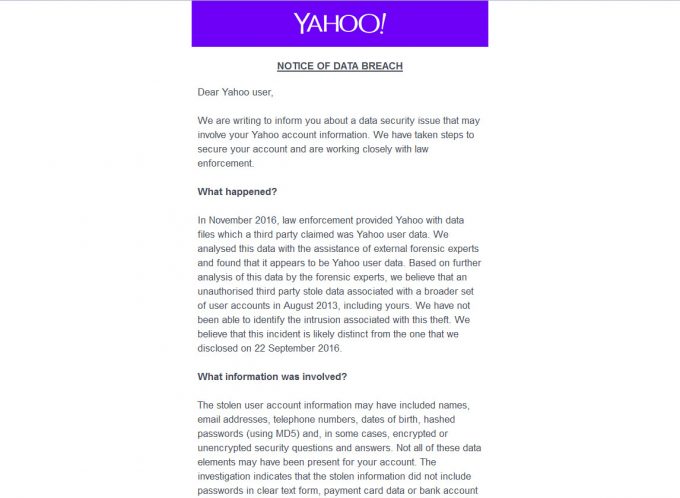
If it was a genuine security issue, they would be forward with the details and ask you to contact them directly. And if it relates to email security, you’ll receive and email notifying you (like above), such as with the recent Yahoo leak. Yahoo’s email detailing the leak doesn’t provide links for you to log in either, you must do that yourself, and yes, that really is for security (since you shouldn’t click links in emails unless you know exactly where it goes).
For any Yahoo email account holders out there that read this, and you are wondering if the call you received was genuine – no, it wasn’t. If you already handed over bank details, call your bank immediately. For everyone else, stay safe… and maybe migrate away from Yahoo entirely.
Support our efforts! With ad revenue at an all-time low for written websites, we're relying more than ever on reader support to help us continue putting so much effort into this type of content. You can support us by becoming a Patron, or by using our Amazon shopping affiliate links listed through our articles. Thanks for your support!