- Qualcomm Launches Snapdragon 4 Gen 2 Mobile Platform
- AMD Launches Ryzen PRO 7000 Series Mobile & Desktop Platform
- Intel Launches Sleek Single-Slot Arc Pro A60 Workstation Graphics Card
- NVIDIA Announces Latest Ada Lovelace Additions: GeForce RTX 4060 Ti & RTX 4060
- Maxon Redshift With AMD Radeon GPU Rendering Support Now Available
Arm Creates Framework For Security As Standard In IoT Devices
This is one of those things that’s been a long time coming, yet still can’t get here soon enough. While the IoT revolution is lauded as both a blessing and a curse, one critical aspect has had more than its fair share of news coverage, and that’s security. Arm (yes, it’s Arm now, and not ARM) wants to put a stop to the blatant disregard for basic security by setting up a standardized framework for all IoT devices to follow, that will prevent the torrent of security leaks that happen on a daily basis.
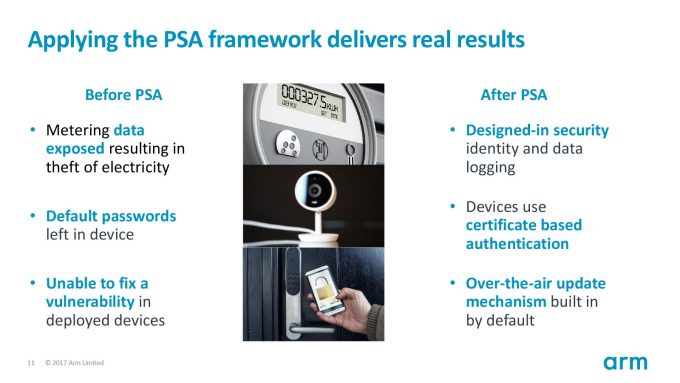
Nearly every day, some kind of security flaw is discovered that can affect millions of devices. While many of those flaws can be patched, there is a growing number of devices containing the worst flaw of all, no security at all. Baby monitors and home security systems, Bluetooth locks and printers, all happily broadcasting private information over the Internet for anyone to see, and the owners probably don’t even know.
Despite the prevalence of these flaws, manufacturers continue to make and sell products with laughable security, such as non-encrypted logins, identical factory set passwords, and unprotected firmware that can be easily overwritten. While a single device by itself might seem innocuous, it can be taken over by hackers (or even not-so-sophisticated scripts) and re-purposed for something more nefarious, such as turning a brand new fridge or FitBit into a zombie for DDoS attacks.
Arm wants to put security into the heart of the design process by creating not only a framework, but a reference model for how to implement basic security practices when designing the next generation of IoT devices. Arm’s Platform Security Architecture (PSA) will be finding its way into Cortex-M processors, the type used in most IoT devices, and will have a number of design requirements and firmware to help reduce complexity and costs in building secure devices. The firmware specifications will also be open source. Devices built using Arm’s mbed OS will have these security features baked in going forward.
Some of the core aspects that make up PSA include device identity, making each device unique to prevent spoofing. Implementing a trusted boot sequence so that man-in-the-middle attacks can not inject code at boot time. Secure, over-the-air updates on all devices so that any vulnerabilities can be patched without replacement (such as with vulnerabilities with Bluetooth locks). Finally, certificate based authentication, to prevent the practice of using passwords for logins, so only authorized users with the correct (and unique) key can access a device.
That last part has an extension as well, Arm SDC-600. Using certificates to authenticate access solves one problem with unauthorized access, but for more hardened devices, an extra layer is required, and that’s not only to prevent access to software, but also prevent access to the firmware, namely, debuggers. This sort of stretches into DRM territory, preventing people taking advantage of debug ports on devices and reflashing a device, such as to unlock additional features on TVs.
PSA already has a huge list of supporters from industry giants, across a wide range of platforms and devices, so we expect to see these enhanced security measures rolled out over the next generation or two of products. Unfortunately though, standardizing the process of security still ultimately require the design team to implement the security features correctly. Arm does enforce certain hardware requirements for PSA to work, most of which are rolled into the ASIC design process, or via a dedicated security module that can be tacked on, such as with its TrustZone CryptoIsland-300 on-die package. However, it will still be possible to follow standards, yet implement them incorrectly – just read into how easy it is to screw up SSL on websites.
Security shouldn’t be optional, especially with the number of Internet-enabled devices, and PSA is a much needed step in keeping people safe. All of these security measures can, and should be, in use on more advanced devices, such as smartphones, and is available across all of Arm’s architectures. PSA’s initial roll-out will focus on the aforementioned Cortex-M series first, which is mostly used for IoT, a category that Arm expects to expand exponentially over the coming years. With the recent announcement of royalty free chips becoming available, and now PSA going open source, the next wave of devices should be both cheaper, and more secure – at least, in theory.