- Qualcomm Launches Snapdragon 4 Gen 2 Mobile Platform
- AMD Launches Ryzen PRO 7000 Series Mobile & Desktop Platform
- Intel Launches Sleek Single-Slot Arc Pro A60 Workstation Graphics Card
- NVIDIA Announces Latest Ada Lovelace Additions: GeForce RTX 4060 Ti & RTX 4060
- Maxon Redshift With AMD Radeon GPU Rendering Support Now Available
Believe It Or Not: Randomly Dropped Malicious USB Flash Drives Still A Real Problem
Considering the fact that it’s 2016, it might be easy to assume that most people out there understand the basics of PC security, such as: don’t pick up a random flash drive and plug it in. That has been an established issue, but it hasn’t been that common in the real-world.
Google has just proven that there is in fact still a risk, however. At BlackHat, Google’s Elie Bursztein, who’s part of the company’s anti-abuse team, talked of a test conducted at the University of Illinois’ Urbana-Champaign campus – and the results are kind of shocking.
Of the nearly 300 USB flash drives speckled about the campus, 98% were picked up, and with a staggering 45% of them, someone not only plugged the drive in, but started carelessly opening the files found on the drive.
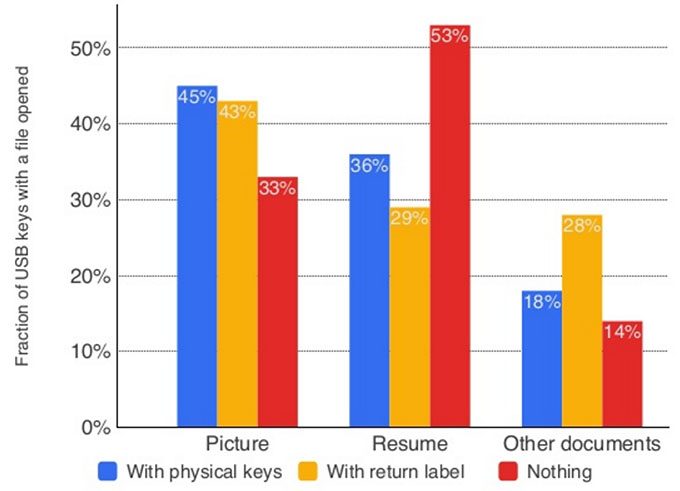
The risk here should be obvious: it wouldn’t be complicated for someone to create a batch of these flash drives with malicious files on them, which could lead to software issues, or even worse, potential identity theft.
It’s not hard to understand why this kind of attack is so successful. As humans, we’re all curious. If we find a wallet, most will look inside to see who it belongs to before handing it over to a lost-and-found department. The same applies to a USB flash drive. Just what could be in there?
In this particular case, Google laced the flash drives with HTML files disguised as images and documents. If any one of these files were opened, an image would load from a remote server, which is what helped Google keep track of how many of these drives were accessed. At that point, the finder was asked to complete a survey, with the promise of a gift card, to explain why they decided to plug the drive in and explore it.
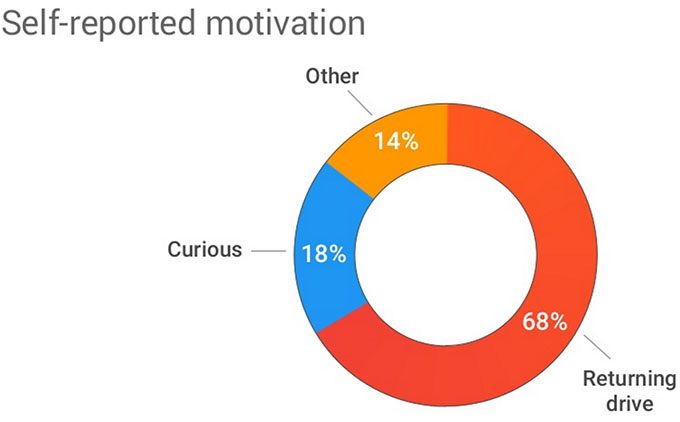
20% of those who found a drive agreed to do the survey, and 18% of those admitted to being “curious”, while two-thirds said that they were looking for details about the drive’s rightful owner, so as to return it to them.
The lesson here? Don’t pick up random USB flash drives, and if you do, make sure you access it in a “clean” environment, such as inside of a virtual machine that doesn’t have access to the rest of your PC. Even then, you should exercise caution. It could be that the drive doesn’t just include files, but a rootkit, as explained in Bursztein’s detailed blog post. Play it safe!




