- Qualcomm Launches Snapdragon 4 Gen 2 Mobile Platform
- AMD Launches Ryzen PRO 7000 Series Mobile & Desktop Platform
- Intel Launches Sleek Single-Slot Arc Pro A60 Workstation Graphics Card
- NVIDIA Announces Latest Ada Lovelace Additions: GeForce RTX 4060 Ti & RTX 4060
- Maxon Redshift With AMD Radeon GPU Rendering Support Now Available
Brian Krebs’ Website Taken Offline Through Massive DDoS Attack, Google Swoops In To The Rescue
It’s been quite the week for security journalist Brian Krebs, but not for great reasons. Well – that can be subjective, as some good is coming out of the unparalleled DDoS attack his website KrebsOnSecurity encountered last week.
Let’s rewind a little bit. Earlier this month, Krebs wrote a story about vDOS, an illegal service that allowed paying customers to take websites and services offline through a DDoS attack. The reason vDOS was in the news at this particular time is because it suffered a database leak, with the goods finding their way to Kreb’s hands. Naturally, Krebs reported on the leak, and that was that.
If only it were so easy. At around the same time, two Israeli teens were deemed responsible for the service and were subsequently arrested. Fast-forward to late last week, and Kreb’s website suffered a DDoS attack of unparalleled proportions: it sustained traffic of over half a terabit per second.
To put the attack into perspective, many Internet users enjoy connection speeds of around 50Mbps. You’d need more than 10,000 such connections to pull off this kind of attack. Lucky enough to have a 1Gbit connection, a la Google Fiber? You’d still need more than 500 such connections to match the kind of traffic Kreb’s website suffered.
Ultimately, Akamai, the company that provided the backbone for Krebs’ website, was forced to boot him from its services, as the inundation of traffic managed to affect its other customers. Krebs doesn’t fault Akamai for this move, though it is unfortunate that he was given almost no time to migrate his website off of its network.
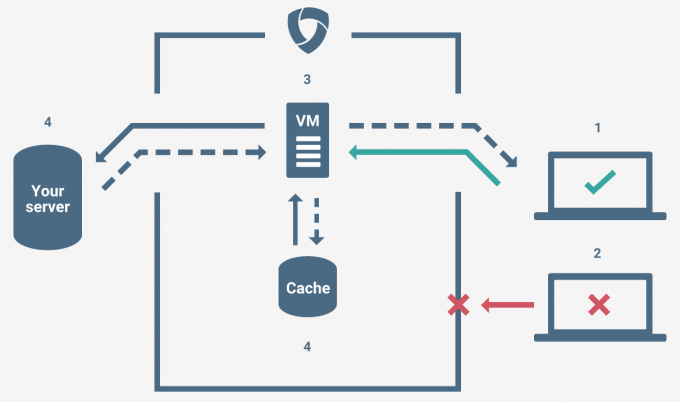
Today, Krebs’ website is back online, and in a new post, he details why. This time, it was Google that came to the rescue, as with its Project Shield program, it decided to pick Krebs up on the basis that he was being censored through these attacks. Clearly, Google has an incredible infrastructure, and handles countless DDoS attacks on its own at any given time. It’s good that such a service is offered.
Interestingly, before I could finish writing this post, Krebs’ website went back offline, although directly-linked images still work. The site was online and working just fine as I began this post, but in a matter of minutes, it went back offline, with a 503 error. It wouldn’t be surprising if Krebs’ website continued to be hit with a DDoS attack, but it’s hard to tell at this point if the problem right now is related to that, or if the site is still being reconfigured.
Nonetheless, this issue highlights a severe one: people who disagree with what’s being said online can take matters into their own hands and take down an entire website or service with relative ease. In this case, it’s good that vDOS’s owners are likely to face some justice, but we’d be naive to think that this issue will stop there.
When Krebs’ website becomes operational again, you can read his latest post right here.