- Qualcomm Launches Snapdragon 4 Gen 2 Mobile Platform
- AMD Launches Ryzen PRO 7000 Series Mobile & Desktop Platform
- Intel Launches Sleek Single-Slot Arc Pro A60 Workstation Graphics Card
- NVIDIA Announces Latest Ada Lovelace Additions: GeForce RTX 4060 Ti & RTX 4060
- Maxon Redshift With AMD Radeon GPU Rendering Support Now Available
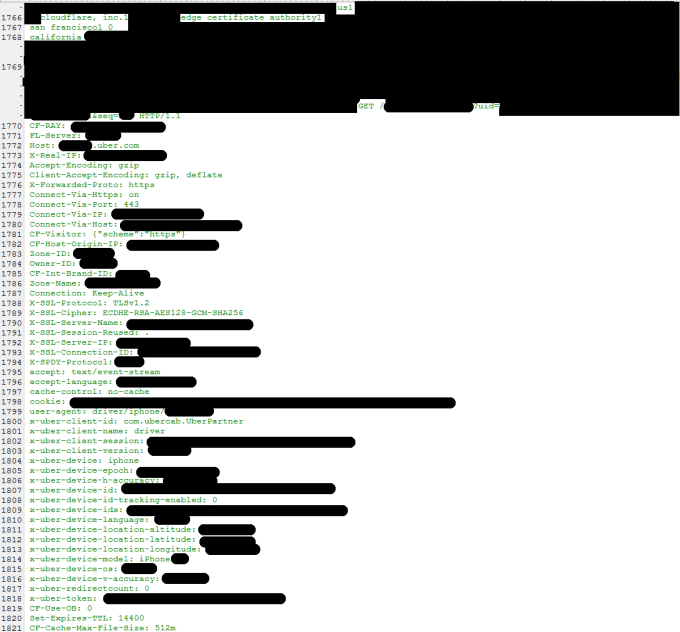
Cloudflare Exposes Sensitive Data In Massive Cache Leak
In probably the biggest security breach that’ll happen this year, web cache service Cloudflare has been leaking text messages, cookies, passwords, IP addresses and other sensitive data for the last few months (the issues were only just brought to light).
Exposed by Google engineer Tavis Ormandy, the now dubbed Cloudbleed bug was the result of a poorly configured parser used by Cloudflare to modify web pages to include Google Analytics tags, convert HTTP links to HTTPS, as well as obfuscating sensitive data seen by bots (such as email addresses and phone numbers).
The reason for the name Cloudbleed is that there are a number of similarities with the Heartbleed incident which exposed sensitive data in memory on the server when using OpenSSL. In this case, the HTML parser would include random blocks of other site’s cached data when served up on a site with three specific Cloudflare features enabled.

To understand the issue, we need to look at what Cloudflare does first, and that’s to act as a giant web cache for millions of websites (often referred to as a CDN, or Content Delivery Network). When a user visits a Cloudflare enabled website, they are instead redirected to Cloudflare’s servers first, where a recent cached version of the page is served instead of connecting to the original host directly. This means Cloudflare takes the brunt of the traffic, with the client’s server mostly sitting idle, saving huge amounts of bandwidth, and often speeding up the viewer’s browsing experience (since the cache could be local to them, rather than the server on the other side of the planet).
Cloudflare also provides a number of other services beyond just acting as a dumb cache. It also provides a number of extra utilities, such as the aforementioned email obfuscation, but also render-blocking CSS and JavaScript correction, HTTPS rewrites, and inserting Google Analytics code on all requests.
The parser used by email obfuscation, Server-side Excludes and Automatic HTTPS Rewrites would leak extra information from the server’s memory; cached data from other sites running through Cloudflare. Websites that used those three services could trigger the bug and cause the data to leak.
What makes this issue worse is that search engines and other web caches and archive sites would then also save this cached version of the page, effectively putting all this potentially sensitive information on publicly accessible web caches. Anyone with some Google-Fu could then use search engines to trawl through the leaked info.
That leaked data could (and did) include passwords, messages sent over OKCupid, session tokens by Uber, and other miscellaneous data. The full extent isn’t known just yet.
You can read up on all the details on Cloudflare’s blog post, as John Graham-Cumming goes through the caching process, what caused the issue, and the severity. Also included is a number of code samples and the NGINGX configuration.
Tavis also has the original bug report that you can read into. This is also where he lists some of the Uber session tokens that were leaked, with cookie information, and OKCupid messages.
While various search engines have already purged their caches, a number of web archives may still hold onto that data. To be clear, while the bug was activated on certain sites with specific Cloudflare options enabled, it is not just those sites affected. Any site that uses Cloudflare services could have data leaked as a result of this bug.
Since there are a large number of sites that use Cloudflare, the possibility for exploitation is massive, and a number of sites are already telling customers to change passwords, including password management system, 1Password. If sites did security properly, the passwords leaked would not be plain text, but encrypted. However, you should consider those passwords invalid and changed anyway.
So far, there is a list of known affected sites (some of them are subdomains of larger sites, so keep that in mind) and if you have accounts with those sites, it would be best to change passwords. Notable sites include Uber, FitBit and Discord. Be aware, these are only known sites, it’s possible any other site that used Cloudflare could be affected.