- Qualcomm Launches Snapdragon 4 Gen 2 Mobile Platform
- AMD Launches Ryzen PRO 7000 Series Mobile & Desktop Platform
- Intel Launches Sleek Single-Slot Arc Pro A60 Workstation Graphics Card
- NVIDIA Announces Latest Ada Lovelace Additions: GeForce RTX 4060 Ti & RTX 4060
- Maxon Redshift With AMD Radeon GPU Rendering Support Now Available
Why Do So Many Companies Not Care About Strong User Account Security?
Companies that seem to not care too much about user security is a major pet peeve of mine, and after updating a password on a certain website this morning, I wound up feeling compelled enough to rant about it. So here we are.
Aeroplan is a flight rewards program like many others, and while it feels like it’s joined at the hip with Air Canada, both companies are independent (Aeroplan is owned by Aimia). Despite this, an Aeroplan number is required to log into Air Canada’s website, which means that customers share the same login and password for both services. That’s a fair enough design in general, but I feel there are faults with this one.
Until earlier, I had been using the same password for Aeroplan for way too long. While I keep individual passwords for services I use, I don’t update them all on a regular cadence. With Aeroplan, I felt compelled to update the password simply because my miles are beginning to become substantial.
It didn’t take long to spot the first issue:

It’s 2017, and here’s a service that has an imposed cap on the length of your password. Further, it can’t include special characters, and has to include at least one number and letter. Ironically, despite the forced format, Aeroplan recommends that you choose a password that’s not “easy to guess”.
What this ultimately means is that every single Aeroplan and Air Canada customer has a password between 6 – 10 characters with at least one number and letter that doesn’t include a special character. Those are the kinds of restrictions that brute-force attackers grin about.
At least the usernames are unique, right? Nah. As an Aeroplan number is required to login, that means 100% of Aeroplan / Air Canada customers login with a series of 9 numbers; eg: 123 456 789. While it’s very unlikely anyone would try to brute force the logins (generally attackers will already have the logins, either through previous knowledge or because a database leaked), the username scheme here further shows how dumbed-down this protection is.
What concerns me isn’t that someone will barrage Aeroplan’s servers with a brute-force attempt (I’d hope Aeroplan would have generic protection for this in place), but rather that someone will attack the company’s servers and run off with the database full of user logins and their hashed passwords. It seems like every single day a company falls victim to this kind of attack. Even security firms have been affected. What makes Aeroplan special?
I’d love to stop here, but there’s another thing I decided to investigate. If someone breaks into an Aeroplan account, they’re not going to simply book a flight, because while they could (probably), that booking is always going to be tied to the Aeroplan number, so that’s one sure-fire way to get caught. However, what if rewards are opted for instead?
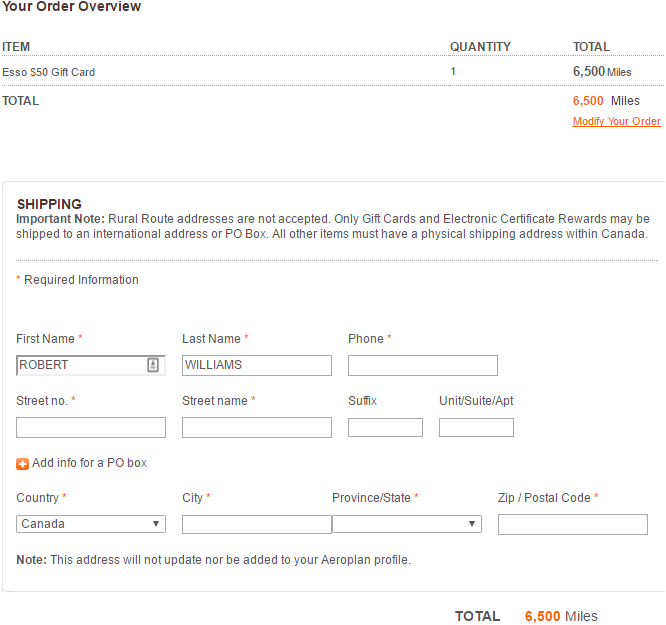
The screenshot above shows the process of ordering a $50 gas gift card. You’ll note that it’s not required to be sent to me, but instead can be mailed anywhere. This means that if Aeroplan’s user database leaks to the Web, and attackers manage to brute-force some accounts, gift cards or merchandise could be ordered and sent to an address that’s not the owner’s.
I should note that this issue isn’t remotely exclusive to Aeroplan; it just happens to be the company I ran into that has what I feel are awful security measures. Even if the service offered 2 factor authentication (it does have a mobile app), that’d be a huge improvement. Alas, there is no such thing.
Why am I ultimately concerned about this? As someone who sees database breaches happen all of the time, I don’t feel safe knowing a meager password with archaic restrictions is all that protects the travel miles I’ve accrued, or my entire Air Canada account, for that matter. This kind of security could have been deemed acceptable 15-years-ago – it certainly isn’t acceptable now.
This begs the question of “why?” Why do so many companies put in such little effort to protect their users? Laziness? Not wanting to spend? It’s hard to say, but what I know for sure is, database breaches are never going to stop, so any company with a modicum of respect for its customers should at least do the bare minimum to give them the impression that their data is safe.




