- Qualcomm Launches Snapdragon 4 Gen 2 Mobile Platform
- AMD Launches Ryzen PRO 7000 Series Mobile & Desktop Platform
- Intel Launches Sleek Single-Slot Arc Pro A60 Workstation Graphics Card
- NVIDIA Announces Latest Ada Lovelace Additions: GeForce RTX 4060 Ti & RTX 4060
- Maxon Redshift With AMD Radeon GPU Rendering Support Now Available
Addonics CipherUSB Review – Portable Encryption Made Easy

As important as data encryption can be for the home user, it’s even more imperative in the enterprise. The problem? The most effective measures are usually cast aside in lieu of something a little easier to deal with. With the CipherUSB, Addonics hopes to bring “simple” and “most effective” together as one. Does it succeed?
Page 1 – Introduction, Uses & Setup
It doesn’t take a very deep search through my article history to know that I’m a big security nut. I live and breathe it for much of my job, given the sensitive data that I work with. These habits have followed me home, with the likes of encrypted drives, encrypted SSH tunnels, HTTPS protocols for all Web-based stuff. It’s not just paranoia anymore, of course… it’s pretty clear at this point (as Edward Snowden has proven) that “they” are listening – to you, to me, to everyone.
This digital, always-on and always-exposed world has led to a new push for security at more than just the major corporation level. Churches, community organizations, small businesses, and even individuals need to start taking more control over their digital fingerprints. However, anyone who has bothered with even the simple concept of PGP for his or her email knows what a pain it can be to truly live and interact with a secure environment.
Addonics Technologies, a company that focuses on storage technologies and enclosures, has aimed to make that simple in the US market with its release of the CipherUSB dongle family. The CipherUSB is designed to provide AES256 ECB or CBC encryption to either entire partitions (FDE, or full-disk encryption) or at the file/folder level (FLE, file-level encryption), and can feature either one-factor or two-factor authentication (we’ll get into that in a second) and optional built-in storage. Pricing, of course, varies by which of those options you choose, but ranges reasonably from $30 to $80.

What’s important and different about the CipherUSB suite isn’t that it encrypts with AES256 or that it has so many options. You can take a stroll through Newegg and see all sorts of encryption-enabled HDD cases, USB drives, and etc. What made us stop and say “I want to look at it,” came down to a promise from Addonics that I’ve never found to be true about encryption: it’s reusable across multiple devices, and it’s easy to use. Coming from a business environment where users constantly want skip or simplify passwords to make them faster to type or bypass one more prompt, where biometrics are too finicky to reliably use, and where nobody can find the same USB stick twice in an hour… many of us have been in that environment. Having something that actually promises to be easy and versatile as well as secure seems like a dream come true.
A brief note about important encryption concepts
Before you can effectively determine your encryption needs, you need to start with an understanding of a few basic encryption concepts. The most basic fact of all is that encryption must be reversible – whatever you encrypt must be able to be decrypted again. This makes encryption much more difficult (and different from) its cousin, the hash, which can (and should!) mangle data to an irrecoverable state.
Other terms of note include:
- Authentication “Factors” – We should only be able to decrypt data if we are supposed to, which means we need a way to authenticate ourselves. There are three general factors we can use – something we know (a password, a pin number, etc), something we have (a card, a dongle, a USB drive, a key, etc.), and something we are (retina, fingerprint, etc.). Out of those three, we can have one-, two- or even three-factor authentication. Most of us are familiar with one-factor (your password to log into your email or voicemail) and two-factor (your debit card) authentication that we don’t even think of it.
- Encryption “Levels” – The term “Encryption level” tends to conjure the idea of difficulty to decrypt the data, but it really isn’t. Encryption levels define how much of a system is encrypted at once (and therefore how much of the system needs decrypted at once to access it). For instance, FDE (full disk encryption) means that the entire block device (a fancy word for partition, like your “C:” drive) will be encrypted at once with the same algorithm. You can’t tell what’s been stored because the files, file table, and everything that could define any individual unit within the drive becomes encrypted with it; but, conversely, the same decryption used to get one file can get ALL files. FLE (File Level), on the other hand, encrypts only specific files/folders on your drive individually – but their existence is verifiable.
- Encryption Algorithms – There are a ton of these out there, and each one is different. Suffice it to say that AES256 is the encryption of choice right now, as it is not “breakable” (defined as being able to be decrypted any faster than bruteforcing the password) by any current means. AES256 comes in many flavors (known as “modes”), with the most common being ECB and CBC. ECB has fallen out of favour as it is by far the weakest of the options, but let’s be realistic… the difference between these at present is like saying “from here to Pluto,” and “from here to Alpha Centauri” in security. Both are really, REALLY far and we aren’t getting there anytime soon. For those who just have to know a little more detail, ECB basically encrypts your data block by block through the AES algorithm once, while CBC encrypts it, then encrypts each block of the encrypted function again. ECB can expose some or all of the key if your data contains long groups of repeating characters. Being as AES256 already sends your data through its mills 14 times in one pass, CBC could be considered overkill for today’s processes… but it may not be that way in the future!
- Encryption Methods – There are two main methods of encryption – symmetric and asymmetric. Symmetric, also known as “private key,” is the oldest form of cryptography and involves one “key” that is given to all people who would need to decrypt the data. This method is used to restrict access, and is what storage encryption uses. Asymmetric, or “public key,” creates two keys – one key unique to the creator, and another key able to decrypt the data but that cannot replicate the creator’s key for encrypting. This method is used in communications (PGP, HTTPS, VOIP) to authenticate the sender and receiver as well as restricting the access.
The CipherUSB Family
So, with the basics covered, let’s take a look at the offering from Addonics. The CipherUSB comes as either a pass-through dongle (which we love) or sealed with flash storage. Whichever you choose, you will have the option for one-factor or two-factor encryption and ECB or CBC algorithms. As noted above, ECB is weaker – and in file-level storage, could even be considered unwise. This is because ECB encrypts every block of every file the same way, meaning that someone with access to a file with a large amount of repeating patterns (or several small files with similar patterns) can possibly begin to deconstruct the key. CBC will make sure this is impossible.
The CipherUSB FDE Passthrough model is the commercial release of the Enova Enigma (Addonics is Enova’s strategic partner for peripheral and storage releases). The crux of the unit is the Enova X-Wall DX chip, which offers hardware-based encryption at up to 40MB/sec throughput. The FLE Passthrough models (I have the ECB single-factor version for testing) sport the same design. Because the FLE requires software to determine which files to encrypt/decrypt, it works only on Windows/Mac (Mac is optional and costs extra), but the FDE design will work on any host system once initialized.
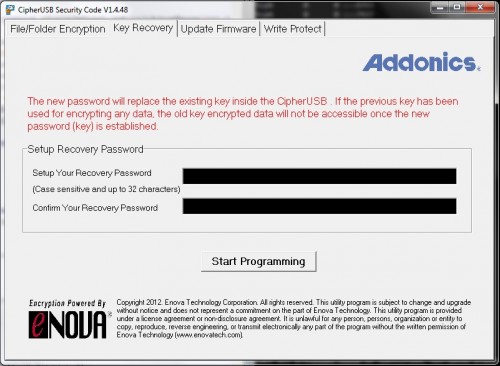
Each CipherUSB model becomes initialized with a password, and that password does not have to be unique. This password is used to develop the actual key (I won’t get into detailing how, for security reasons) that is written via firmware to an otherwise inaccessible EEPROM chip on the device. This string then becomes the key for encrypting/decrypting files through the device. The cipher key will be incredibly strong, as it is a PRODUCT of your password instead of just the password itself padded to the correct key length. It will also never be made available to any host system, as it’s hard-wired directly to the encryption chip and never needs to be loaded into host memory anywhere.
Why am I telling you all of that boring stuff? To point out one of the best strengths/weaknesses of the device – any CipherUSB of the same model family, programmed with the same password, can open an encrypted file or device. That makes it incredibly useful in a corporate setting, so long as you choose and protect your passwords carefully – you can share those passwords between groups of people to create simple but highly effective layers of security, and not have access tied to just one device. If a CipherUSB gets lost or stolen, you can just order a new one and be back up and rolling in no time. And as we’ll cover later, programming the device with a new password is very quick and easy, so you don’t need every person on staff to each have their own dongle.
The CipherUSB does come with one other interesting set of features, which I will skip past in my review below because I’m not terribly sure of their usefulness with this device’s target market. The features involve setting write protections on the USB drive that is connected to the device, either to the MBR (master boot record) or the entire device. This allows “auditing” of an external disk without altering it, and (according to the instructions) “protection from viruses”… an interesting feature, but one that I can’t for the life of me think why I would need on a device like this.
Setting up the CipherUSB
To use the dongle, you must connect the CipherUSB to some kind of USB drive (the actual device is immaterial) to initialize it. On Windows, it will auto-mount a read-only partition and ask you to run the initialization tool. Enter a pass-phrase twice, hit the button, and your device is ready to use!
For FDE single-factor authentication, you’re all set now aside from formatting the USB drives you want to use with the dongle. On FDE two-factor authentication, you’ll still need to re-open the program and type your password each time you insert it with an encrypted USB drive into your system, but otherwise you’re ready to roll. That’s it – no drivers, no headaches, no nothing. Insert, and get on with your life – anything saved to the drive will be automatically and transparently encrypted. If the USB drive is connected to a computer without the CipherUSB in between from then on, it will show up solely as an unformatted drive (as Windows won’t even be able to read the partition table). Thus ends the tour of the FDE model (and why we told Addonics we really would rather see the FLE model).
I’ll make one more mention of the FDE units (particularly single-factor models) that I find really slick in a corporate environment, and that’s daisy-chained encryption. Give two differently encoded units to different people, and require both of them present to open a drive – effectively requiring two people to collude in order to edit, copy or otherwise misappropriate the data. This is hardly “revolutionary” security, but it’s seamless, and business people like seamless things. If both units plug into each other (in the right order) and the drive is plugged into that, it will work like nothing is out of the ordinary. Plug either unit in or both in the wrong order, and you’ll see nothing. You can do the same with the FLE models by simply encrypting a file and then encrypting it again under a different key, but it’s really slick how transparent it can be in FDE mode.
Support our efforts! With ad revenue at an all-time low for written websites, we're relying more than ever on reader support to help us continue putting so much effort into this type of content. You can support us by becoming a Patron, or by using our Amazon shopping affiliate links listed through our articles. Thanks for your support!