- Qualcomm Launches Snapdragon 4 Gen 2 Mobile Platform
- AMD Launches Ryzen PRO 7000 Series Mobile & Desktop Platform
- Intel Launches Sleek Single-Slot Arc Pro A60 Workstation Graphics Card
- NVIDIA Announces Latest Ada Lovelace Additions: GeForce RTX 4060 Ti & RTX 4060
- Maxon Redshift With AMD Radeon GPU Rendering Support Now Available
TrueCrypt Primer: Part 1 – What It Is & Why You Should Care

We’ve talked a lot in the past about keeping your computer safe and data backed-up, but we haven’t delved much into keeping your data secure. In this first part to a three-part series, we’re taking a look at one of the best (and easiest-to-use) cross-platform solutions for keeping your important data encrypted: TrueCrypt.
Page 2 – TrueCrypt Volumes
TrueCrypt uses the concept of virtual disk volumes to help create, use and manage encrypted data. TrueCrypt volumes behave exactly as if a new disk drive had been installed on the system and, once mounted, can be accessed through normal file browsing tools (Windows Explorer, Mac Os X Finder and Linux ls command, for instance).
When you require a file or folder/directory to be encrypted, you simply mount your TrueCrypt volume of choice and move the file or folder/directory inside there. For all purposes, a TrueCrypt volume, once mounted, is entirely transparent to the user and the operating system makes no distinction between it and a regular disk drive on your computer. In parts II and III of this series you are going to learn exactly how these volumes are created and managed. TrueCrypt’s interface makes this a simple procedure.
TrueCrypt makes a distinction between three different volume types: File Hosted Volumes, Partition Hosted Volumes and Pre-Boot Authentication Volumes.
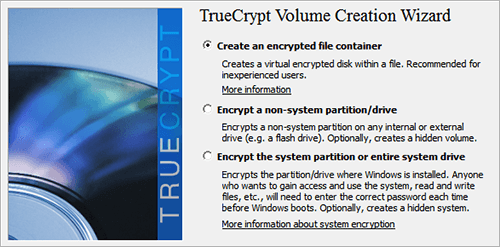
The three types of TrueCrypt Volumes
File Hosted volumes (known also as Containers) are virtual disk volumes represented by a single file on your computer, very similar to mounting an ISO file as a virtual drive on your computer. These volumes are the ideal choice if you do not want to encrypt the entire device or disk partition, but wish to have a file containing encrypted data inside. By far, this is the most common usage of TrueCrypt. File Hosted Volumes are an excellent option for sensitive or personal data that you wish to store in cloud-based Internet services like DropBox, SkyDrive or Google Drive. File hosted volumes are normal operating system files until they are mounted. They can be copied, moved or deleted just like any other file.
Partition Hosted Volumes (or Device Hosted Volumes, if the device contains only one partition) is a disk partition or an entire storage device encrypted by TrueCrypt. These partitions or devices become unrecognizable by the operating system and must be mounted with TrueCrypt before they can be used. This is an ideal choice when you want to encrypt an entire USB memory stick or other external storage devices. It is also the volume you should create when you wish to have an encrypted hard drive (or partition) for the single purpose of storing any sensitive data.
Pre-Boot Authentication Volumes are used when you wish to encrypt the entire system drive where Windows resides. They aren’t volumes per se since they aren’t mounted on a running operating system, But allow me to make the distinction since, on the case of system partition, TrueCrypt refers to it simply by the process name (System Encryption) and doesn’t name the resulting encrypted partition.
System encryption is discussed in more detail in part III of this series.
Plausible Deniability
TrueCrypt introduces in its arsenal of security features the concept of Plausible Deniability. The term refers to the ability of denying the existence of any encrypted data when being forced to reveal its authentication password under threat. TrueCrypt achieves this with Hidden Volumes.
TrueCrypt allows you to create Hidden Volumes when specifying the creation of Partition Hosted Volumes or when encrypting the operating system. A hidden volume is implemented by wrapping the encrypted volume you want to hide inside another TrueCrypt volume. The volume you want to hide is also moved to the free space area of the outer volume. TrueCrypt makes this easy to achieve through its wizard. Note that both the outer volume and the hidden volume must have different passwords. These passwords should also be significantly different.

TrueCrypt hidden volume creation
The outer volume can contain some files that you will be able to reveal if forced to give a password. Ideally, these should be files that represent a security concern to you, in order for your deniability to remain plausible. However, after opening the outer volume, other than those files, all your opponent will see is empty space — unknowing to him that that empty space is in fact another TrueCrypt volume that requires another password to decrypt.
The empty space on a hard drive or any other storage media is usually represented internally by seemingly random data, especially after doing a disk wipe. This is exactly what an encrypted volume looks like. So you can safely give your password away for the outer volume and convince your opponent there is nothing more to it (admittedly, plausible deniability is 10% technological trick and 90% good acting).
However, the plausible deniability of TrueCrypt has been under the close scrutiny of security analysts. Some deficiencies have been pointed out. The most glaring one may be the fact that TrueCrypt volumes invariably pass two tests that attempt to introduce the concept of Probable Cause against that of Plausible Deniability. Namely, TrueCrypt volumes sizes are divisible by 512 and they pass a Chi-Square randomness test. In the presence of this, there may be some reasonable suspicion that the empty space is in fact a hidden volume (or for any purpose, encrypted data). More so if we consider TrueCrypt hidden volumes are a known feature of the program.
You can always argue you used a tool to wipe that empty space and that is the reason why it passes those tests. This strengthens the argument for plausible deniability because there are in fact disk wiping tools that specifically do this. But the truth of the matter is that a minimum amount of reasonable doubt should only deter law enforcement officials, not criminals trying to extort information from you.
Support our efforts! With ad revenue at an all-time low for written websites, we're relying more than ever on reader support to help us continue putting so much effort into this type of content. You can support us by becoming a Patron, or by using our Amazon shopping affiliate links listed through our articles. Thanks for your support!




